Top Guidelines Of Disaster Recovery
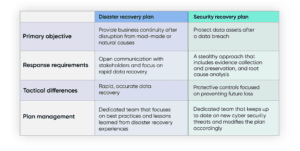
company connection: Know the difference In the company globe, catastrophe recovery is often utilized mutually with organization connection (BC). While these terms are comparable, there are some important differences to keep in mind: Service connection relates to keeping a company functional when a catastrophe strikes Catastrophe recuperation concentrates on recovering accessibility to data as well as IT facilities adhering to a physical or virtual incident As a best practice, you must have enhanced service continuity as well as calamity healing plans in place to maintain procedures and restore access after a triggering occasion.
Reputational harm Companies are likewise in jeopardy from reputational damage adhering to a long term interruption. After all, individuals today have high assumptions and also expect immediate and also dependable access to on the internet solutions, 1 day a day. When customers can not access on the internet resources, they have unfavorable experiences. Relying on how negative it obtains, they may despair in the brand name, grumble on social media, and also potentially also switch to rivals.
With this in mind, IT calamity recovery normally centers around the adhering to tenets. Know what you don't understand Businesses commonly assume they have the resources as well as methods they need to effectively recuperate from a calamity. Firms today are highly dynamic. IT landscapes adjustment by the hour as new individuals, information, and also connected systems sign up with the layer.
Things about Disaster Recovery
Businesses often tend to make the mistake of thinking service companies and also partners have failproof strategies, which leads to problems. It's much more secure to form a strategy instead of counting on various other agencies for service continuity.
Post-disaster After the calamity ends, staff member require to know when to return to normal workflows and also relocate off backup systems. As soon as the calamity remains in the rear-view mirror, you must proceed replication to make certain you are still syncing to backup systems. At the end of the procedure, it's crucial to debrief the objective.
Disaster Recovery Fundamentals Explained
This will assist visit this site to focus on disaster healing preparation. Examining as well as evaluation Once you have a viable catastrophe healing strategy in location, your business will require to function to evaluate as well as upgrade it (disaster recovery). As a best method, you need to test as well as upgrade your calamity recuperation plan every six months. By screening and also evaluating your catastrophe recuperation strategy, you can make sure that it matters and up to speed with the present requirements of your organization.
The faster you respond to a cyber occurrence, the much less damage it will cause.
By currently, we have actually all listened to stories concerning ransomware and the crushing effect it can have on little organizations. Just like a lawbreaker can hold a person hostage in exchange for money, hackers can hold your most vital information and also need payment.
Prep work is crucial when it involves reducing the results of a possible ransomware assault. A Calamity Recuperation Plan is basically a tactical plan for exactly how to handle a ransomware strike (or other kind of cyber strike), need to one happen. A strong plan, combined with preventative safety and security services, avoids your service from dealing with tragic consequences at the hands of a hacker.
The Best Guide To Disaster Recovery
Your plan needs to make from this source up every department within your company and be tested to ensure your whole group knows exactly how to react in the occasion of an unexpected strike. Maintain these ideas in mind when creating a first-class Calamity Recovery Strategy: Your plan ought to include each of the adhering to important elements: Goals for healing that are clear for every department within your organization, As discussed above, this ought to consist of,, as well as you will certainly need in case of a catastrophe.

DRPs have actually ended up being a staple in modern-day business. Below are the crucial elements of a catastrophe recuperation plan design template and why they're essential.
Preparation is vital when it involves mitigating the effects of a prospective ransomware assault. A Calamity Recovery Plan is essentially a strategy Get the facts for exactly how to handle a ransomware assault (or other kind of cyber strike), ought to one occur. A solid plan, combined with preventative safety solutions, stops your service from facing devastating repercussions by a hacker.
The smart Trick of Disaster Recovery That Nobody is Discussing
Your strategy should comprise every single division within your company as well as be checked to guarantee your whole team knows exactly how to react in the event of an unanticipated assault. Keep these pointers in mind when establishing a top-notch Calamity Recuperation Strategy: Your plan ought to consist of each of the following important elements: Goals for healing that are clear for every division within your company, As discussed over, this must consist of,, and also you will certainly require in the occasion of a catastrophe.
The key to restoring your systems rapidly is to avoid any type of confusion and obtain everybody on the exact same web page as very early as feasible following an attack. You must additionally have a clear understanding of who requires to be contacted in the occasion of an event and also exactly how they can be reached.
DRPs have actually become a staple in contemporary company. Right here are the essential aspects of a catastrophe healing plan theme and why they're necessary - disaster recovery.






